Cross Domain Solutions: Keeping Data Safe Across Boundaries in a Zero Trust world
As digital ecosystems grow more complex and collaborative, the secure exchange of data across networks with different trust levels has never been more critical.
This challenge is particularly crucial for government, defense, and critical infrastructure organizations, where classified and sensitive data must move safely between domains without compromising confidentiality, integrity, or national security.
Cross Domain Solutions (CDS) are specifically designed to enable secure data exchange between isolated networks with differing classification levels. But as file-based threats grow in complexity and subtlety, even well-established CDS technologies must evolve to keep up.
Understanding Cross Domain Solutions
At its core, a Cross Domain Solution is a cybersecurity architecture that enforces policy-based controls over data transfer between different security domains. These domains may range from highly classified government networks to public-facing systems used by coalition partners, contractors, or civilian agencies.
The primary goal of a CDS is to prevent data leakage and block unauthorized access or malware infiltration, ensuring that only approved and secure information crosses boundaries. This is particularly vital in environments where a security breach can have significant diplomatic, operational, or even life-threatening consequences.
Why CDS matters in government and critical infrastructure
Governments around the world rely heavily on CDS to manage data flow between national security systems and operational environments. Whether supporting battlefield communications, intelligence sharing, or critical infrastructure monitoring, these solutions help maintain mission assurance by mitigating risk at one of the most vulnerable junctions where networks intersect.
For example, a defense agency may need to receive geospatial data from an unclassified source and then process or combine it with classified operational information. Without a robust CDS, this interaction could expose sensitive assets to external threats. In sectors like energy, transportation, and emergency services, the stakes are similarly high, as cyberattacks on control systems could disrupt entire cities.
Key components of a CDS
To meet strict security demands, a CDS usually incorporates a combination of technical and process-lead safeguards. At a high level, these components include:
- Policy Enforcement
CDS systems enforce pre-defined security policies to ensure that data transfers comply with organizational, national, and international regulations. These rules dictate what types of data can move between domains, under what conditions, and how that data must be handled.
- Filtering and Validation
Content inspection mechanisms validate that files or messages do not contain prohibited formats, malware, or unauthorized information. These controls help prevent data leakage or command-and-control attacks hidden within benign-looking files.
- Content Transformation
Data is often sanitized or reformatted to strip out potentially harmful elements such as embedded scripts, macros, or non-standard structures that could be exploited.
- Auditing and Logging
Every file movement is logged and auditable to provide traceability, accountability, and assurance. This is essential for incident response and compliance audits.
- Controlled Interfaces
Physical or logical network boundaries are implemented to ensure that only the CDS governs traffic between zones. These interfaces are hardened to prevent bypassing.
Modern CDS deployments may also integrate with broader cybersecurity frameworks, such as Security Information and Event Management (SIEM) systems, to provide continuous monitoring and incident detection.
The growing threat of file-based attacks
While many CDS deployments are robust, a persistent challenge lies in managing file-based threats, especially those that evade traditional detection tools.
Files remain a primary vector for cyberattacks. Threat actors commonly hide malware within PDFs, Office documents, images, and archives. These malicious payloads can be embedded using techniques such as steganography, obfuscation, or exploitation of zero-day vulnerabilities.
Standard antivirus and sandboxing tools can struggle with these advanced threats, particularly when operating within high-security environments that cannot tolerate detonation or latency. Even technologies such as Data Loss Prevention (DLP) may fail to identify sensitive information embedded deep within document layers or hidden in metadata and comments.
This “file-based threat gap” creates significant risk for CDS architectures that rely solely on detection-based security mechanisms. A single compromised document passing through a CDS can open a critical network to espionage, sabotage, or ransomware.
A shift toward Zero Trust in CDS
To address this gap, many organizations are aligning their CDS strategy with a Zero Trust cybersecurity model. Rather than assuming that a file is safe once it passes initial inspection, Zero Trust treats all content as inherently suspicious until proven otherwise.
This model aligns closely with the "trust no file" approach, where security mechanisms verify not only the sender and metadata but also deeply inspect or rebuild the actual file content before it is allowed to cross into a higher-trust environment.
Key to this approach is the adoption of advanced content filtering and transformation technologies. These technologies don’t rely on signature-based detection but instead rebuild files according to known-good standards, removing any active content, hidden data, or non-compliant structures. The result is a clean, standardized file with preserved usability and drastically reduced risk.
Use case: secure collaboration between allied agencies
Consider a scenario where a national defense agency needs to share operational documents with allied forces operating in a joint mission. The source system may reside on a classified domain, while the receiving network is only cleared for limited access.
In this case, a CDS ensures that the document is stripped of any classified content, macros, or hidden code before it's transferred. It may also perform natural language processing (NLP) checks to identify restricted terms or redact sensitive personal information (PII) such as names, IDs, or location markers.
This not only maintains the confidentiality of the source network but also protects the receiving network from potential compromise.
CDS challenges and evolving standards
Implementing a CDS can sometimes be complex because the balance between security and usability is delicate. Too much restriction may hinder productivity or delay time-sensitive operations, while too little control risks exposing secure environments to attack.
Furthermore, global initiatives such as the U.S. National Cross Domain Strategy & Management Office (NCDSMO) have introduced frameworks like Raise the Bar to improve the baseline for CDS implementations. These initiatives encourage vendors and implementers to adopt more robust evaluation, assurance, and mitigation strategies.
Such standards are crucial, as they drive industry-wide improvements and reduce fragmentation in how cross-domain threats are addressed. Still, many organizations find it challenging to both comply with these standards and keep pace with real-world operational needs.
The future of Cross Domain Solutions
As cyber threats grow more advanced and international collaboration becomes more essential, Cross Domain Solutions will become more central to national cybersecurity strategies. Future CDS technologies are expected to incorporate greater automation, AI-driven threat detection, and improved user experience to ensure secure data transfer without operational bottlenecks.
We can also anticipate deeper integration with Zero Trust architectures, especially at the file and endpoint levels. Security must now move with the data itself, rather than remaining only at the network perimeter. This requires a change in thinking in how file trust is earned, validated, and enforced.
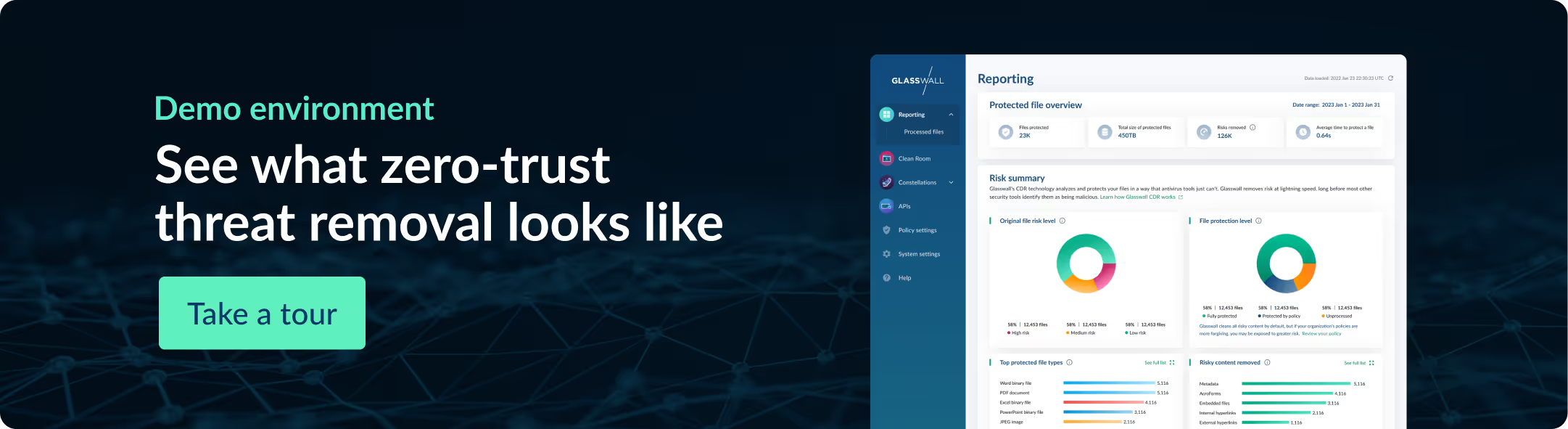
How Glasswall supports secure Cross-Domain file sharing
Glasswall brings a unique approach to strengthening Cross Domain Solutions by aligning with the Zero Trust principle of "never trust, always verify." Rather than detecting threats, Glasswall’s Content Disarm and Reconstruction (CDR) technology proactively rebuilds files to a known-good state, removing risky elements without sacrificing usability.
This ensures that all file-based content moving through a CDS, whether Microsoft Office documents, PDFs, or images, is rendered safe by design. Glasswall's technology also integrates seamlessly with existing CDS frameworks, supports air-gapped or tactical deployments, and meets the strict requirements of initiatives like Raise the Bar.
By providing complete transparency, policy control, and verifiable outcomes, Glasswall empowers government and critical infrastructure organizations to operate with confidence in high-stakes environments.
Ready to modernize your cross-domain security?
Discover how Glasswall eliminates file-based threats through a Zero Trust architecture.