File-based threats are on the rise: key security insights for your organization in 2025
Despite advances in Zero Trust frameworks, one threat vector continues to bypass even the most advanced detection systems: files.
Malicious actors are leveraging everyday document formats to deliver sophisticated and undetectable payloads, successfully evading defenses even in environments equipped with EDR and XDR tools. These endpoint detection and response and extended detection and response solutions are designed to monitor and analyze activity across endpoints and networks, but they often fall short when threats are embedded in seemingly benign files.
The Glasswall Security Research Team analyzed intelligence reports from 2025 to highlight how file-based threats have evolved and why traditional detection is no longer enough.
To understand the scale and nature of the risk, let’s break down what the latest data shows.
PDFs have become a top choice for cyber attackers
PDFs now account for nearly half of all malicious file samples analyzed across multiple threat intelligence reports and sources, such as Check Point, SonicWall, and IBM.
Once viewed as trusted and stable, PDFs are increasingly being weaponized to conceal active code, scripts, and exploits that evade detection.
This trend reveals a fundamental weakness in signature and behavior based tools such as EDR and XDR. Attackers no longer rely on known malware patterns. Instead, they exploit legitimate file structures and zero-day vulnerabilities that detection systems cannot yet recognize.
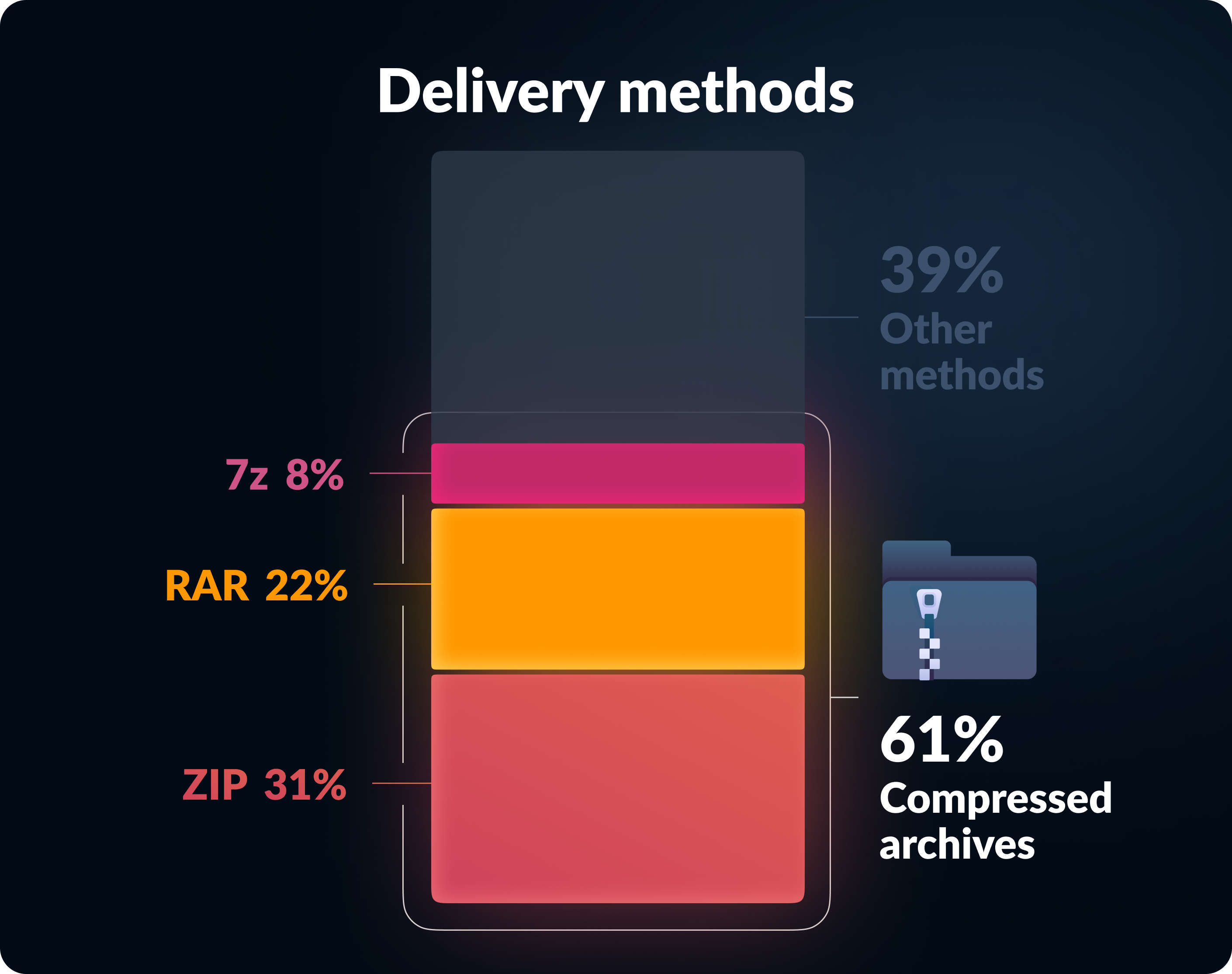
Archives are a growing malware hotspot
Compressed archives remain another common attack method. Around 31 percent of malicious samples are hidden in ZIP files, 22 percent in RAR, and 8 percent in 7z formats. These containers easily pass through perimeter and endpoint controls because their content is compressed, encrypted, or disguised as legitimate business material.
“Traditional detection engines struggle to inspect files at this level without disrupting workflows or introducing latency,” said Connor Morley, Head of Security Research at Glasswall. “Attackers take advantage of that gap while also relying on the fact that organizations routinely trust these formats in everyday operations. The result is a blind spot where malicious content can pass through multiple controls before a user unknowingly triggers the attack.”
Vulnerability exploitation and human error continue to fuel attacks
According to Verizon’s 2025 Data Breach Investigations Report unpatched software and human error are still key drivers of breaches. Sixty percent of incidents involve users unintentionally triggering an attack, while vulnerability exploitation now accounts for 20 percent of all breaches, a sharp year-over-year increase of thirty four percent.
These patterns show that even with EDR/XDR and threat intelligence integrations in place, organizations remain exposed. Human behavior and unpatched systems cannot be detected away.

Third party and ransomware risks are escalating
The risk extends beyond internal users. Breaches involving third party suppliers have doubled since last year, representing 30 percent of all incidents. Ransomware appeared in 44 percent of breaches, a 37 percent rise, often delivered through compromised files shared across trusted networks.
This highlights the need for proactive protection at the file level rather than reactive detection after a compromise has occurred.

Why detection alone is not enough
EDR and XDR platforms are vital for visibility and incident response, but they depend on detection. They identify threats once there is a known signature, behavioral pattern, or post execution signal. In contrast, file-based attacks often arrive in clean looking documents with no recognizable malicious behavior until it is too late.
“This is where Content Disarm and Reconstruction (CDR) provides a critical layer of defense,” said Paul Farrington, Chief Product and Marketing Officer at Glasswall. “By removing ambiguity around what a file contains, CDR ensures only trusted, fully reconstructed content reaches the user. This shifts the balance from reacting to threats to eliminating them before they ever appear on a detection timeline.”
How Glasswall keeps your organization ahead of file-based threats
Glasswall’s Zero Trust file protection technology takes a proactive approach to file security. Instead of trying to detect threats, it rebuilds every file to a known safe standard. Embedded scripts, macros, and active content are automatically removed, and the file is reconstructed to maintain full functionality and fidelity. The result is a clean, trusted version of every file, ready for safe use.
By focusing on file safety rather than detection, Glasswall closes the gap that Antivirus, Sandboxing, EDR and XDR tools cannot cover. As adversaries continue to evolve, relying on detection alone leaves a critical blind spot.
The Glasswall Security Research Team continues to track emerging trends across government and commercial sectors to help organizations stay ahead of evolving file-based threats. If your business depends on files, it is time to rethink how you secure them.
.png)










