10 reasons why you need Content Disarm and Reconstruction
In the contemporary digital landscape, organizations face an ever-increasing challenge of protecting their digital assets from a variety of file-based cybersecurity threats. These threats range from sophisticated malware and ransomware attacks to more insidious dangers, including zero-day exploits, which exploit unknown vulnerabilities in systems. With the rise of remote working and digital collaboration, the frequency of file-sharing has escalated, opening up new avenues for cyber attackers to exploit. Traditional security measures, while essential, often struggle to keep pace with these evolving threats, especially when they are embedded in seemingly innocuous files.
These file-based threats pose a significant risk to organizations as they can lead to data breaches, loss of sensitive information, operational disruptions, and can severely damage an organization’s reputation. The complexity of these threats is compounded by the need to maintain the seamless flow of information – a critical component of modern business operations. As a result, organizations need a cybersecurity solution that not only counters these evolving threats but also aligns with their need for uninterrupted business processes.
This is where Content Disarm and Reconstruction (CDR) technology plays a pivotal role. CDR addresses the core of file-based cybersecurity issues by taking a proactive approach. Instead of merely detecting and blocking known malware, CDR disarms any file entering an organization’s network, deconstructing and reconstructing it to eliminate potential threats while preserving its usability. This approach ensures a higher level of security for file transfers, providing a safeguard against both known and unknown threats. By integrating CDR into their cybersecurity strategy, organizations can enhance their defense posture, ensuring the safe and secure handling of files crucial for their daily operations and long-term success.
Here, we take a closer look at what CDR means in cyber security, how it’s used, and 10 reasons why organizations need it:
CDR use cases:
From government departments to corporate environments, CDR is an important technology for any organization looking to maximize file-based cybersecurity. It can be implemented across a wide variety of use cases to ensure the safe handling of files, performing a crucial role in maintaining digital security and compliance in today's interconnected world. These include:
Cross Domain Solutions (CDS)
Effective CDR can supercharge new and existing cross domain solutions by removing the reliance on detection and data wrapping – replacing it with a zero-trust approach that treats all files as malicious – validating, rebuilding and cleaning each one to the manufacturer’s ‘known good’ specification. This process significantly enhances security in cross-domain communication, crucial in operations involving sensitive data exchange between different classification levels or networks. By ensuring the integrity of transferred data, CDR empowers organizations to maintain operational continuity and data confidentiality in these critical exchanges.

Hardsec
CDR technology can be implemented wherever a file is in motion or at rest. CDR vendors such as Glasswall have developed solutions to enable government departments and corporate organizations to protect key operations with patented and industry-leading zero-trust file protection. This approach is vital for safeguarding sensitive information in scenarios where traditional security measures might fail, such as situations involving advanced persistent threats or sophisticated cyber-attacks. The zero-trust model of CDR ensures rigorous file scrutiny, bolstering defenses against evolving cyber threats.

File upload portals
Ingesting files from external parties and networks is a critical requirement for many organizations and government departments. However, there are weaknesses in current practices that can be exploited by the uploading of malicious content. CDR technologies provide a robust layer of security for file upload portals, crucial for industries including finance and healthcare, where data sensitivity is paramount. By integrating CDR, these portals can ensure that every file received, regardless of its origin, is cleansed of potential threats, thereby safeguarding the organization's digital infrastructure.

Cloud migration
All organizations rely on the transfer of files across trust boundaries, both within their infrastructure or to/from public networks, and it is critical to ensure that malicious content or risky files are not transferred during cloud migrations. Solutions such as Glasswall Halo utilize CDR to offer unparalleled protection during these transitions, a necessity in an era where cloud computing is ubiquitous. By preprocessing files before migration, CDR tools ensure that cloud environments remain secure and compliant – an essential consideration for businesses leveraging cloud technologies for scalability and efficiency.

Isolated networks
Effective CDR provides zero-trust file protection that maintains air-gapped network isolation. Detection-based solutions, in contrast, require an open channel to ingest updates, compromising the isolation of secure networks. The application of CDR in isolated networks is critical for sectors such as defense and intelligence, where network integrity is non-negotiable. By implementing CDR, these networks can confidently manage file transfers without the risk of external threats, preserving the sanctity of their isolated environment.

Industry-critical compliance
To ensure industry-critical compliance, organizations should look for a CDR solution that meets industry guidelines such as the NCSC’s Pattern for Safely Importing Data, the NSA’s Raise the Bar Initiative and the NIST Risk Management Framework by the US Department of Commerce.
Additionally, features such as word search and redact, metadata removal, and image analyzer in solutions provided by CDR vendors such as Glasswall address the growing need for compliance with privacy regulations, including GDPR. This adaptability to various regulatory requirements makes CDR an invaluable tool for organizations operating in regulated industries, where data handling and privacy are closely scrutinized.
10 Reasons why you need CDR
- CDR Prevents Advanced Cyber Threats: CDR can neutralize advanced cyber threats, including zero-day exploits and sophisticated malware, by dismantling and reconstructing files. This preemptive measure is essential in an evolving digital threat landscape where traditional detection-based solutions might not recognize newly developed or highly complex attack vectors. CDR's unique approach ensures that these advanced threats are effectively disarmed before they can infiltrate and harm an organization's digital infrastructure.
- CDR Ensures Secure File Transfer: CDR secures file transfers by disarming and reconstructing files before they enter an organization's network. This process includes removing potentially harmful elements, including macros, scripts, and embedded objects and then rebuilding the files to maintain their usability while ensuring they are free of threats. This capability is crucial in environments where the exchange of digital information is frequent and involves various levels of sensitivity and confidentiality.
- CDR Helps Maintain Business Continuity: CDR technology plays a pivotal role in maintaining business continuity by allowing the safe use of critical documents and files. By ensuring that every file used within the business environment is free of malware, businesses can continue their operations without the interruptions or downtime typically caused by cyber attacks. This reliability is especially crucial for sectors where timely access to information is directly linked to operational efficiency and service delivery.
- CDR Complements Existing Security Measures: CDR boosts existing security measures by adding an additional layer of protection. While tools such as firewalls and antivirus software are essential, they primarily focus on preventing known threats. CDR fills the protection gap by sanitizing files from potentially unknown threats, enhancing an organization's defense against a broader range of cyber attacks and ensuring a more resilient cybersecurity posture.
- CDR reduces dependency on user awareness: While cybersecurity user awareness and training are important, CDR technology significantly reduces the reliance on users to recognize and avoid malicious content. By automatically processing and sanitizing files, CDR minimizes the impact of human error, which is a common cause of security breaches. This feature is particularly beneficial in large organizations where training and monitoring a large number of employees can be challenging.
- CDR protects against targeted attacks: Targeted attacks, such as personalized phishing and spear-phishing campaigns, are designed to bypass standard security measures and exploit specific vulnerabilities. CDR effectively counters these attacks by ensuring that any files received, regardless of their source, are free from hidden malicious content, providing a robust defense against these targeted and often highly sophisticated threats.
- CDR helps deliver zero-day protection: Zero-day attacks exploit previously unknown vulnerabilities, making them particularly challenging to defend against using traditional security measures. CDR addresses this challenge by focusing on the disarmament and reconstruction of files rather than relying on known threat signatures. This approach provides an essential safeguard against these unpredictable attacks, offering protection from the moment a new threat emerges.
- CDR supports compliance and data protection: By preventing malware infections, CDR helps in maintaining compliance with data protection regulations and standards. This aspect of CDR is crucial for organizations handling sensitive or regulated data, as it helps in avoiding the legal, financial, and reputational damages associated with non-compliance and data breaches.
- CDR is calable and flexible: CDR solutions are designed to be scalable and flexible, meeting the diverse security needs of different organizations. The best CDR technologies can be tailored to fit specific security requirements and operational needs, ensuring that as an organization grows or its security needs evolve, the solution can adapt accordingly, providing continuous and effective protection.
- CDR is quick and efficient: CDR processes files incredibly quickly, minimizing delays in accessing content, which is crucial for maintaining efficiency in business operations. In fast-paced business environments, this rapid processing means that security measures do not become a bottleneck in workflows, allowing for seamless and secure access to necessary files and information.
About Glasswall CDR
Glasswall CDR (Content Disarm and Reconstruction) employs our patented 4-step approach to protect organizations and individuals against file-based threats. Unlike most conventional cyber-security solutions, Glasswall CDR does not rely on detection capabilities. Instead, we follow a ‘Zero-Trust’ based approach. Only files that have been Glasswalled have had threats removed. We don’t try to identify malicious code - we simply remove the ability for it to exist in the document.
All files processed by the Glasswall Embedded Engine are assumed to be malicious. The engine will analyze and rebuild the file back to its known-good manufacturer's specification, removing any potential threats lurking in the file’s structure. The act of correcting deeper-rooted structural content is referred to as remediation, whereas removing content which is configurable through policy management (e.g. hyperlinks in office documents) is referred to as sanitization.
The Glasswall CDR engine receives an input file from either a CLI or direct API request to the library. The input file then enters our patented 4-step process to rebuild files back to their manufacturer’s known-good specification.
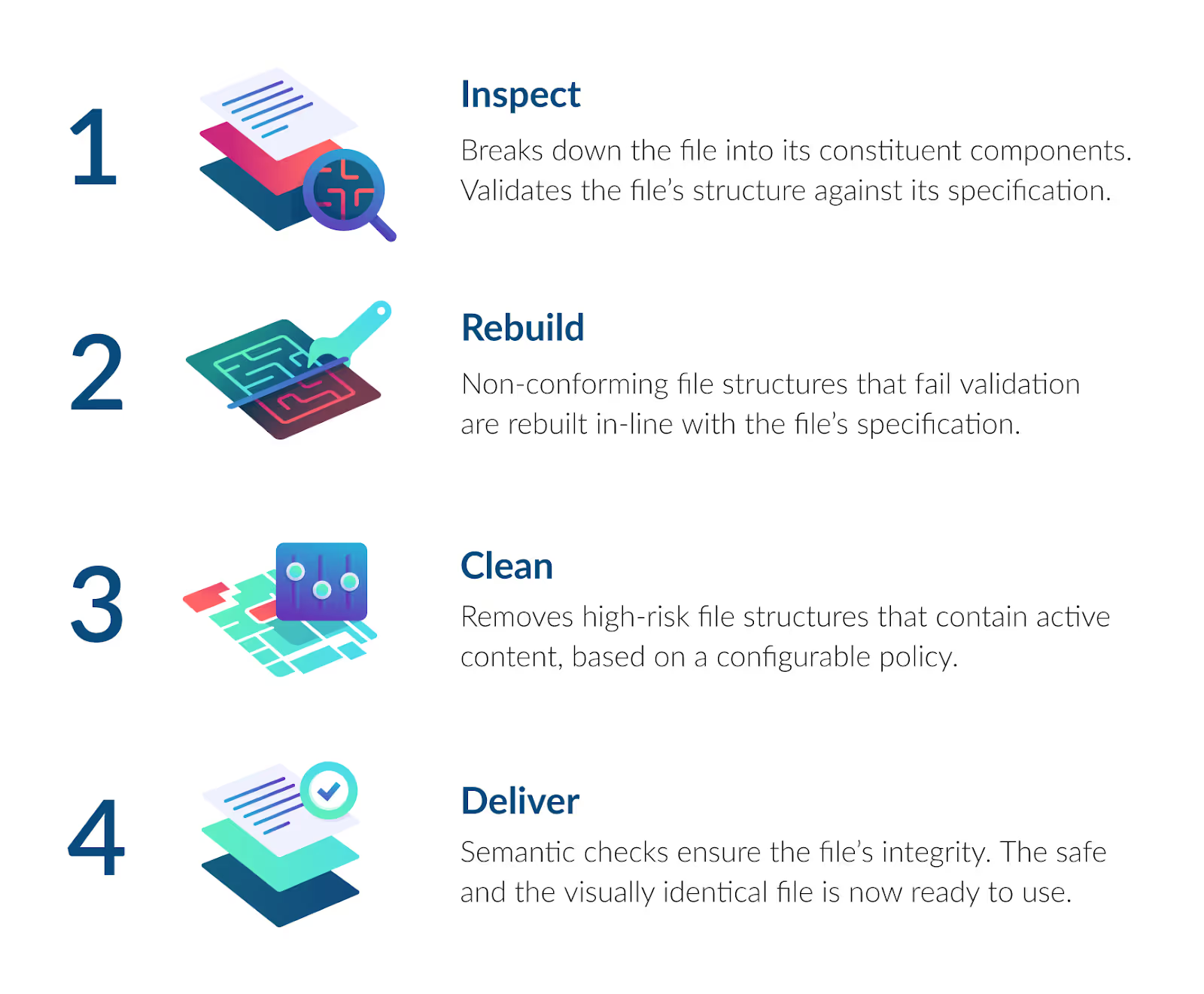
In each of these phases, analysis of the file occurs. The output of each phase then becomes the input for the next, maintaining a level of separation between each process. Once these four process phases have been completed, the Glasswall Embedded Engine generates a pristine file that is free from threats and is accompanied by an analysis report which explains what risks were identified and how these were eliminated.
The safe, ready-to-use file is then delivered to the end user. Alongside file delivery, an in-depth report is provided to the user detailing what changes have been made to the file to ensure it conforms to the required known-good manufacturer's specifications. If the file cannot be processed, the reason for this is detailed to the user.
All of this happens within the Glasswall Embedded Engine, typically in less than a second.









