What is Content Disarm and Reconstruction (CDR)?
File-based cyber security threats are growing faster than ever. Approximately 1 in every 100,000 files contains potentially malicious content, with 98% of them being unknown by antivirus solutions for up to 18 days before they can mitigate potentially devastating risks.
With global trends such as hybrid and remote working continuing to impact the way organizations use technology, the threat landscape is also becoming more sophisticated and complex.
One of the major cybersecurity problems this creates is that existing security solutions fall short, with the widespread reliance on reactive detection-based security, meaning organizations simply can’t keep up with file-based threats.
The Problem With Detection
A major part of the problem is that the use of detection-based security technologies means no matter how complex a solution may be, it can still only protect its users against what has been seen before. For example:

Next generation” AV and firewalls
“Next generation” antivirus and firewall systems use detection-based solutions that can only protect against risks already known to them. This leaves organizations at risk, as bad actors are constantly evolving their techniques and finding new vulnerabilities to exploit.

Machine learning and AI technologies
Machine learning and AI technologies rely on algorithms to detect known signs and patterns of malicious content. While offering a more effective approach than traditional solutions, machine learning and AI on their own cannot offer absolute, zero-trust protection and still leave organizations at risk from new (zero-day) threats.

Sandbox solutions
Sandbox solutions can offer some protection, but cybercriminals now use clever tactics to evade them. Malicious content can be fitted with a delayed ‘detonator’, meaning malware lays dormant and undetected by the sandbox, activating once it passes through.
The shift to proactive protection against file-based threats
Instead of looking for malicious content, today’s advanced CDR (Content Disarm and Reconstruction) technologies treat all files as untrusted, validating, rebuilding and cleaning each one against their manufacturer’s ‘known-good’ specification.
Rather than attempting to detect and block files that are known or suspected to be malicious, CDR rebuilds files and documents into a safe, clean and visually identical ‘known good’ standard that is free from the risks of malware.
The industry-leading CDR solution uses 4-step process to rebuild files back to their manufacturer’s known-good specification:
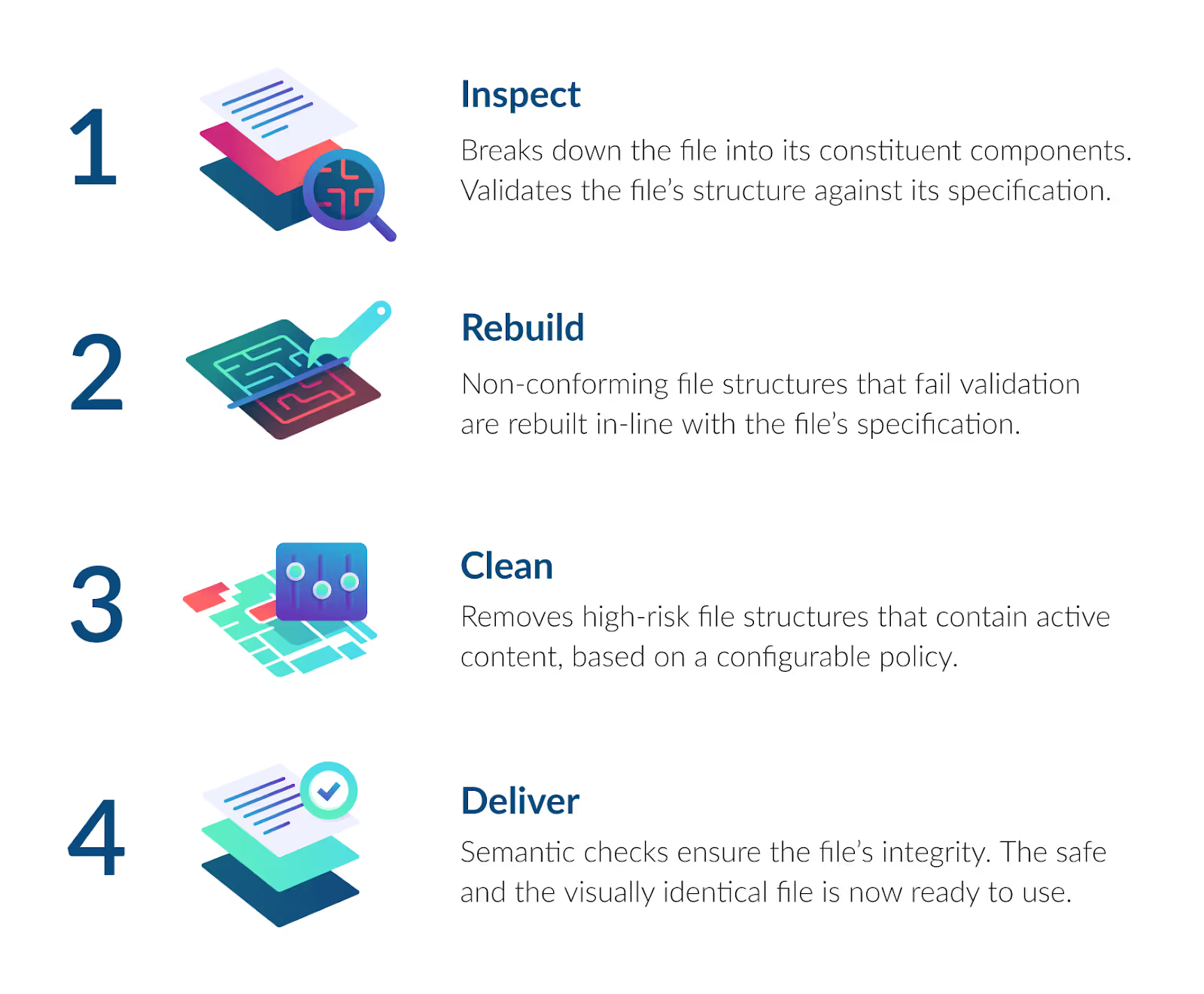
Using CDR means security teams no longer have to choose between complete file security or speed and usability. While some CDR vendors flatten files, the most effective CDR solutions provide rapid zero-trust file protection that maintains original document usability. As a result, there is no dependence on antivirus databases to provide knowledge of a new threat, and security teams no longer deal with disruptions from quarantining files or false positives.
The role of Zero-Trust security
These issues have driven the growing momentum behind the “never trust, always verify” approach to cybersecurity. Also known as the ‘zero-trust’ security model, it is based on the premise that, by default, nothing interacting with IT infrastructure is trusted, regardless of whether it’s inside or outside a network. The phrase was employed by Forrester Research 2010 and has become one of the security industry’s most important approaches to addressing the rising levels of security breaches.

As such, zero-trust sees the world differently from other approaches to cybersecurity as trust boundaries across networks and access points have become increasingly complex and vulnerable to attack.
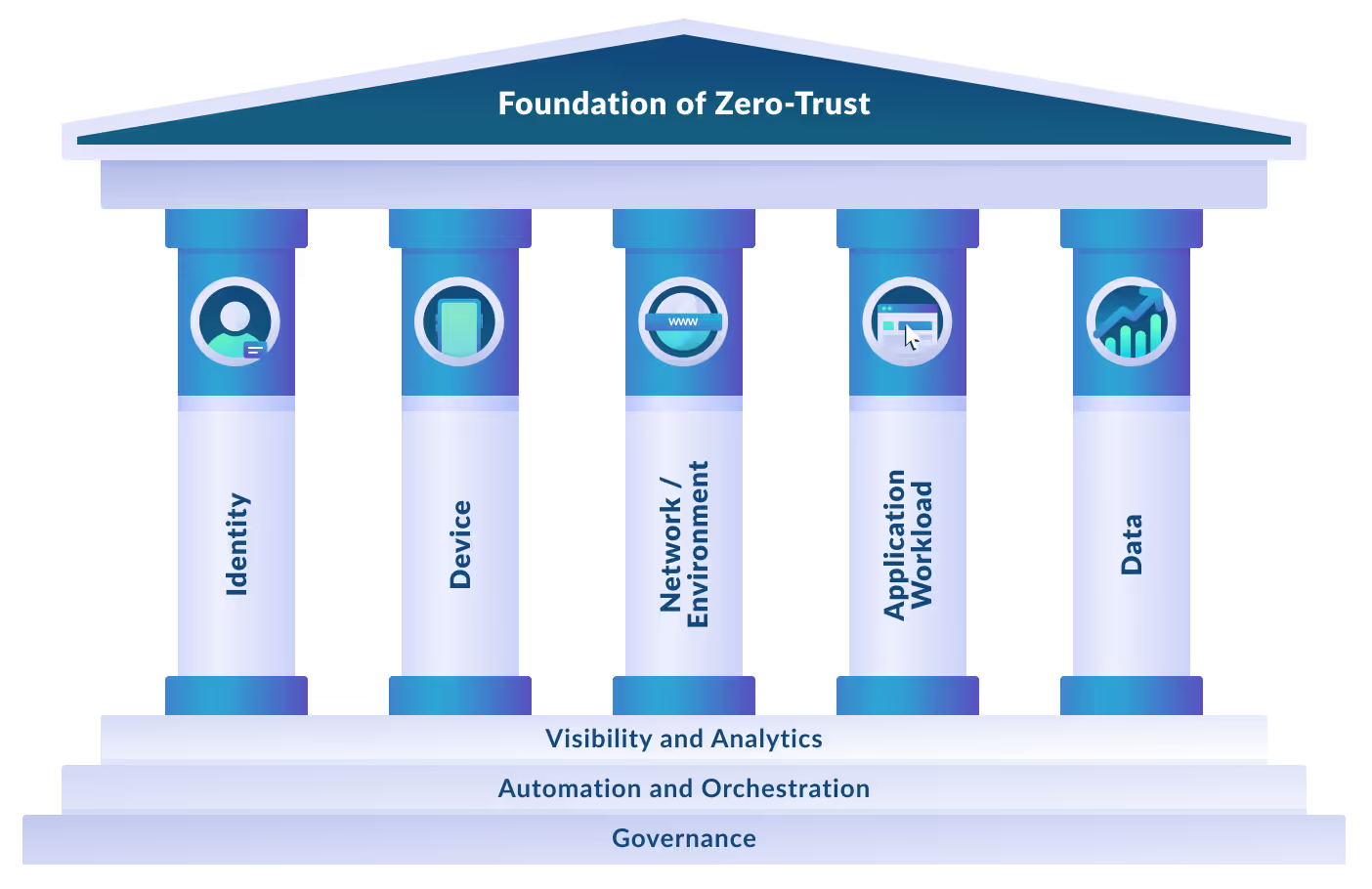
The Five Pillars of Zero-Trust security
But how can organizations get there, and what steps are involved? According to CISA, the foundation of a zero-trust maturity model is represented by five pillars, which include:
- Identity: Identity refers to attributes that uniquely describe users or entities that can introduce risks if not properly managed (such as unauthorized access). Proper identity and access management controls are critical to minimize risk.
- Device: Devices, including hardware, software and firmware that connect to networks expand the potential attack surface. Vulnerabilities in devices like servers, computers, phones, IoT, and more can be exploited if not properly secured and patched.
- Network: Networks and other potential channels like cellular and application-level infrastructure can introduce the risk of data and system compromise that require proper controls.
- Application: Applications and workloads, including systems, programs, and services executing on-premises, mobile, and cloud may contain vulnerabilities that put data at risk if not managed properly. Approaches such as least privilege access and robust authentication help mitigate risks.
- Data: Data in systems, devices, networks, applications, databases, infrastructure, and backups with associated metadata introduces risks, including unauthorized access, if protections like fragmentation controls aren't applied properly. Solutions like CDR that sanitize potential threats in files at rest and motion provide important data security controls.
Why is the Zero-Trust model becoming more important?
Global trends such as hybrid and remote working mean that many networks have become more complex and operate with a greater number of potential attack vectors than ever before.
As a result, cybercriminals have been increasingly successful in exploiting weaknesses in reactive cybersecurity strategies to gain access to networks and data via architectures. In fact, without a zero-trust approach, organizations run the risk of attackers having free reign across a network once they are inside.
In an environment where the threat landscape is becoming more sophisticated, it's easy to understand why many organizations are looking to limit the role of trust in their security strategy.
Add to this the inherent weaknesses caused by ineffective cyber hygiene means organizations are looking to eliminate the security lapses caused by human error and significantly increase their overall levels of protection.
2021’s cybersecurity Executive Order identified zero-trust as an important contributor to cybersecurity best practices. Among its wide-ranging requirements, the EO stipulated that each Federal agency was directed to “develop a plan to implement zero-trust architecture” within 60 days of its publication.
Collectively, these issues are accelerating the adoption of zero-trust. Gartner has predicted that spending on zero-trust Network Access (ZTNA) solutions will rise from $820 million in 2022 to over $1.6 billion just three years later, representing a dramatic acceleration in investment.
CDR use cases in a Zero-Trust world
With zero-trust cybersecurity front of mind for organizations the world over, today’s Content Disarm and Reconstruction technologies have been developed to address a wide variety of use cases. These include:
Cross Domain Solutions (CDS)
CDR technology enables users to supercharge new and existing cross domain solutions, removing the reliance on detection and data wrapping and replacing it with a zero-trust approach that treats all files as malicious – validating, rebuilding and cleaning each one to a known good standard. Read more about CDS>>

File upload portals
Ingesting files from external parties and networks is a critical requirement for many organizations and government departments. However, there are weaknesses in current practices that can be exploited by the uploading of malicious content.
CDR’s zero-trust sanitization capabilities can be established at various integration points within an organization’s security architecture. This provides security teams with the capability to instantly and automatically remove known and zero-day (unknown) file-based threats – delivering secure, visually identical, and fully functioning files to the end user. Read more about file upload portals>>

Cloud migration
All organizations rely on the transfer of files across trust boundaries, both within their infrastructure or to/from public networks, and it is critical to ensure that malicious content or risky files are not transferred during cloud migrations.
Effective CDR provides organizations and departments with REST endpoints that harness the power of the Kubernetes-based CDR Platform. Users can process large storage containers at a massive scale and at lightning speed – ensuring only safe, clean and fully functioning files transfer across networks. Contact us about Cloud migration>>

Isolated networks
CDR provides zero-trust file protection that maintains air-gapped network isolation. Detection-based solutions require an open channel to ingest updates, compromising the isolation of secure networks. Its zero-trust philosophy doesn’t rely on updates to protect against both zero-day and known file-based threats – ensuring maximum isolation for secure networks. Contact us about isolated networks>>

Industry critical compliance
The most effective CDR technologies enable compliance with industry guidelines such as the NCSC’s Pattern for Safely Importing Data, the NSA’s Raise the Bar Initiative and the NIST Risk Management Framework by the US Department of Commerce. Contact us about industry critical compliance>>
Content Disarm and Reconstruction – The benefits
Today, organizations worldwide across public and private sectors see a range of cyber security benefits from using CDR solutions. These include:
Secure & optimize files
By working with safer, more secure files, CDR removes risk and anomalies in an instant, so users can trust every file is safe and usable.
Less risk, more productivity
CDR enhances productivity across the organization by de-risking every document without users ever noticing it is there.
Deploy with ease
Users are up and running in hours, not months and can deploy the solution seamlessly without the typical hidden costs and headaches for their security team.
Check out the comparison between CDR and other cybersecurity solutions








